One-Time Pad Cipher: The Only Mathematically Unbreakable Encryption Method
Here’s the deal—most encryption methods can be cracked with enough time and computing power. But One-Time Pad (OTP) cipher is different. It’s the only mathematically proven unbreakable encryption in existence.
In this guide, we’ll break down:
- ✔ How OTP works (with a step-by-step example)
- ✔ Why it’s “perfectly secure” (and what that really means)
- ✔ Its biggest advantages (hint: no hacker can break it… theoretically)
- ✔ Its fatal flaws (why we don’t use it for everything)
- ✔ Real-world applications (where OTP is still used today)
What is a One-Time Pad (OTP) Cipher?
Developed by Joseph Mauborgne (an Army Signal Corp officer), the One-Time Pad (OTP) is an improvement of the Vernam Cipher. Unlike other encryption methods, OTP is provably secure—meaning no amount of brute force or cryptanalysis can crack it if used correctly.
Key Features of OTP:
- Unbreakable: No mathematical or statistical attack works.
- Random Key: The key is truly random (not pseudo-random).
- Same Length as Plaintext: The key must be as long as the message.
- Used Once: Reusing the key compromises security.
How Does One-Time Pad Encryption Work? (Step-by-Step Example)
OTP uses modular arithmetic (usually mod 26 for letters) to encrypt messages. Here’s how it works:
Encryption Process
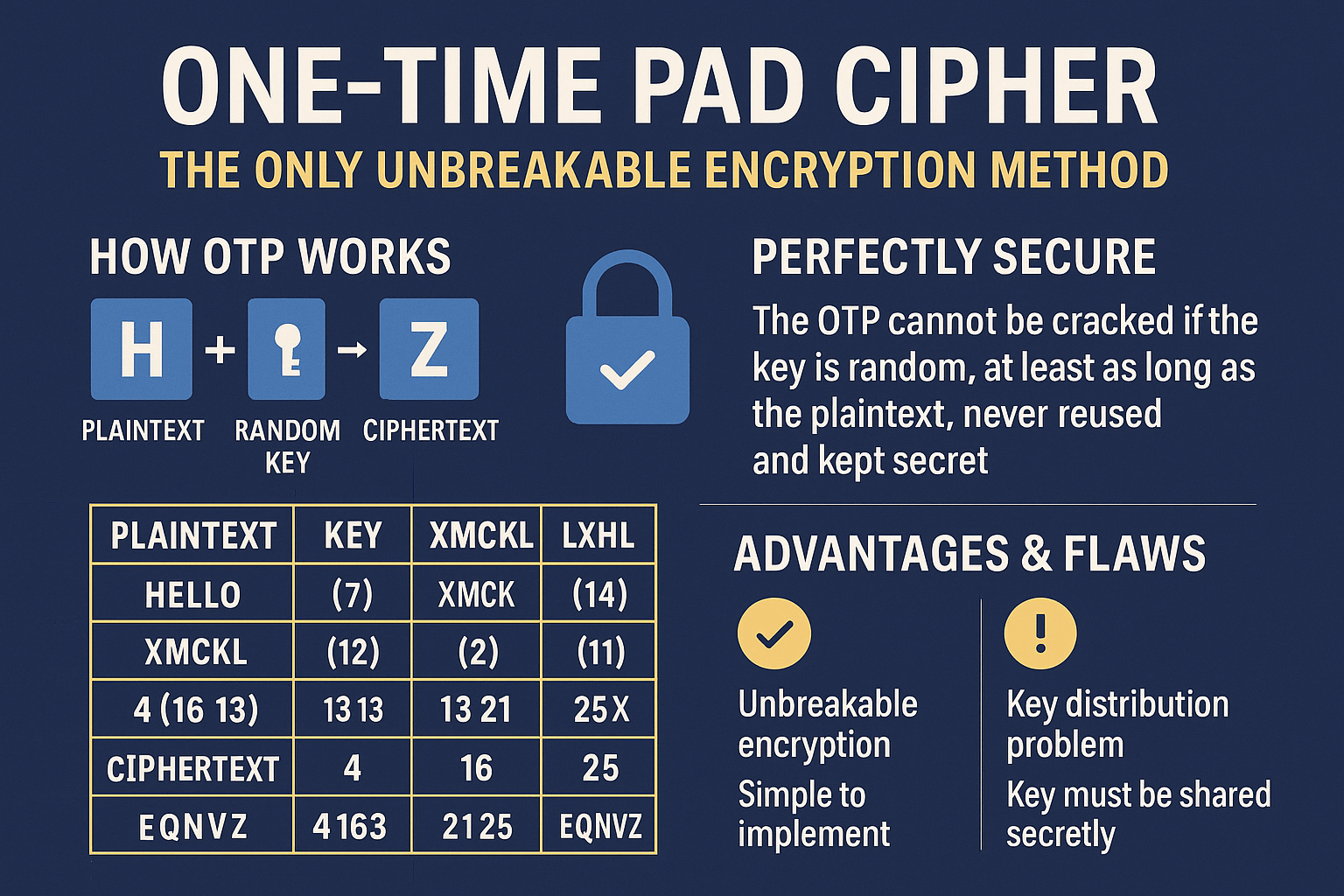
- Assign Numbers to Letters: A = 0, B = 1, …, Z = 25
- Generate a Random Key (same length as plaintext)
Plaintext: HELLO → Key: XMCKL - Add Plaintext + Key (Mod 26):
| Plaintext | H (7) | E (4) | L (11) | L (11) | O (14) |
|---|---|---|---|---|---|
| Key | X (23) | M (12) | C (2) | K (10) | L (11) |
| Total | 30 | 16 | 13 | 21 | 25 |
| Mod 26 | 4 (E) | 16 (Q) | 13 (N) | 21 (V) | 25 (Z) |
Ciphertext: EQNVZ
Decryption Process
To decrypt, just subtract the key (mod 26):
| Ciphertext | E (4) | Q (16) | N (13) | V (21) | Z (25) |
|---|---|---|---|---|---|
| Key | X (23) | M (12) | C (2) | K (10) | L (11) |
| Total | -19 | 4 | 11 | 11 | 14 |
| Mod 26 | 7 (H) | 4 (E) | 11 (L) | 11 (L) | 14 (O) |
Decrypted Text: HELLO
How to Generate a Truly Random Key for OTP (And Why Most Methods Fail)
The biggest weakness of One-Time Pad (OTP) isn’t the algorithm—it’s key generation. If your key isn’t truly random, your encryption isn’t unbreakable.
Here’s the truth: Most “random” keys aren’t random enough for OTP. Let’s break it down.
Hardware RNGs vs. Pseudo-RNGs: What’s the Difference?
Hardware RNGs (True Randomness)
- Source: Physical processes (thermal noise, radioactive decay, atmospheric noise)
- Examples: Quantum RNGs (ID Quantique, QuintessenceLabs), LavaRand (Cloudflare’s wall of lava lamps for entropy)
- Pros: Truly unpredictable (no mathematical pattern), Ideal for OTP
- Cons: Expensive, Slow (generating long keys takes time)
Pseudo-RNGs (Not Random Enough for OTP)
- Source: Mathematical algorithms (seeded with entropy)
- Examples: /dev/urandom (Linux), CryptGenRandom (Windows), Python’s random module
- Pros: Fast & practical for most encryption (AES, RSA)
- Cons: Deterministic (if you know the seed, you can predict the output), Not secure for OTP
“In my experience, 99% of ‘OTP’ implementations fail because they use pseudo-RNGs. If you’re serious about OTP, you need a hardware RNG.”
Why /dev/random and CryptGenRandom Aren’t Good Enough for OTP
| Method | Problem for OTP |
|---|---|
| /dev/random (Linux) | Blocks when entropy is low → impractical for large keys |
| /dev/urandom | Non-blocking, but still pseudo-random (seed reuse risk) |
| CryptGenRandom (Windows) | Better than most, but still relies on system entropy pools |
The Core Issue:
These methods mix pseudo-RNG with system entropy, which works for AES but fails OTP’s “perfect secrecy” requirement.
What to Use Instead?
- Quantum RNG devices (expensive but foolproof)
- Atmospheric noise generators (e.g., random.org)
- Hardware security modules (HSMs) with FIPS 140-2 validation
Can AI Break One-Time Pad? (Spoiler: No, Here’s Why)
Why Machine Learning Fails Against OTP
- No Patterns to Analyze: OTP ciphertext is statistically random (identical to white noise).
- Brute Force is Impossible: A 100-character OTP-encrypted message has 26¹⁰⁰ possible keys—more than atoms in the observable universe.
- Key Reuse is the Only Weakness: AI can’t break OTP, but human errors (reused keys) can.
Real-World Example: The Venona Project
• Soviet spies reused OTP keys in WWII.
• The NSA spent years manually decrypting fragments—but only because of key reuse, not algorithm weakness.
“AI and quantum computing change nothing about OTP’s security. The only way to ‘break’ it is to find a mistake in implementation.”
Why is OTP the Only Perfectly Secure Cipher?
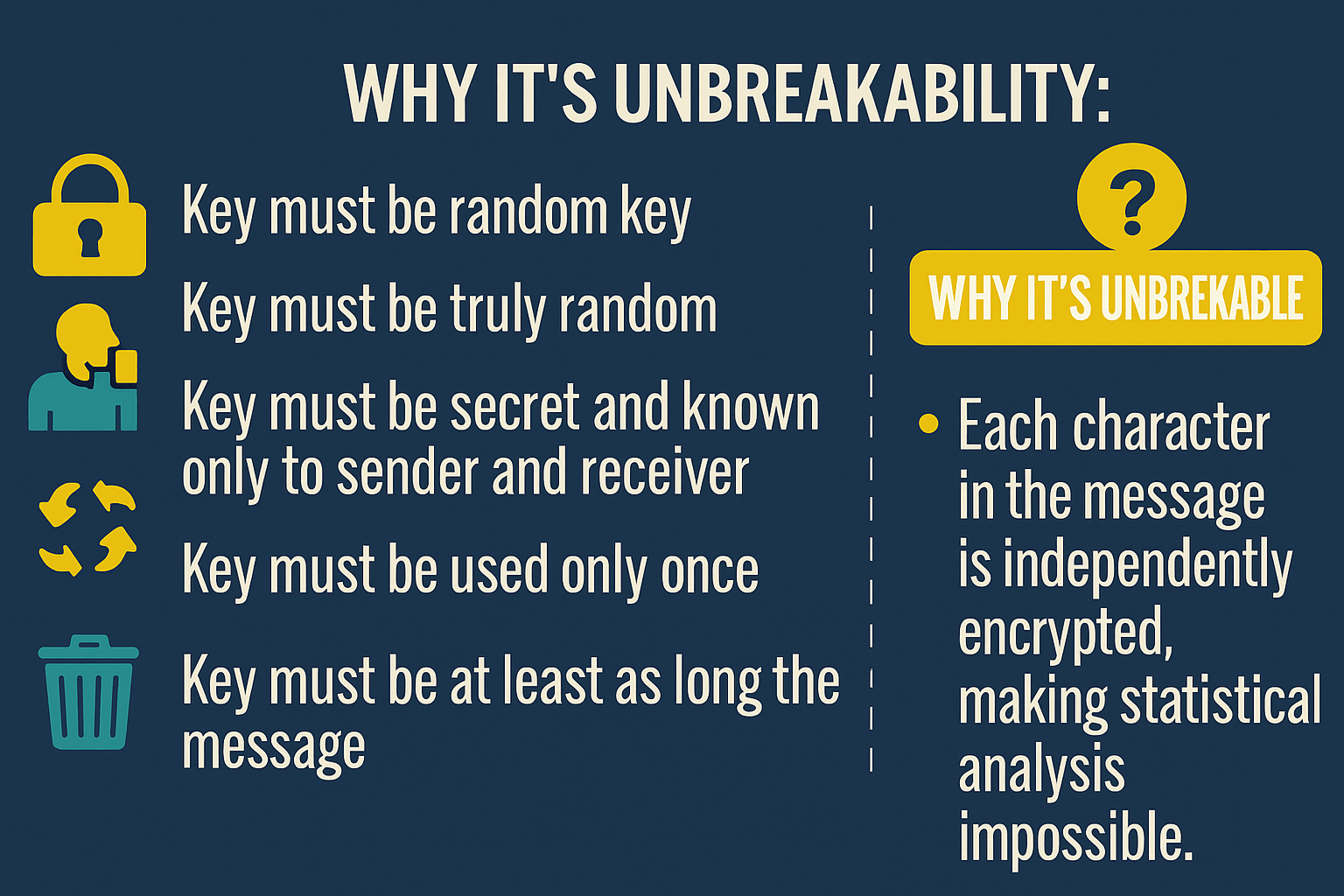
Claude Shannon (the “father of information theory”) proved that OTP provides perfect secrecy if:
- The key is truly random
- The key is as long as the message
- The key is never reused
No other encryption method (not even AES-256) meets this standard.
Advantages of One-Time Pad Encryption
- ✔ Unbreakable (Perfect Secrecy) – No patterns, no statistical attacks.
- ✔ No Mathematical Weakness – Unlike RSA or ECC, OTP doesn’t rely on hard math problems.
- ✔ Unique Encryption Every Time – Even the same plaintext encrypts differently with a new key.
Disadvantages of One-Time Pad (Why We Don’t Use It Everywhere)
- ❌ Key Distribution Problem – How do you securely share a key as long as the message?
- ❌ No Key Reuse – A single reused key breaks all security.
- ❌ Impractical for Large Data – Encrypting a 1GB file requires a 1GB key!
The Limits of Cryptanalysis on Perfect Secrecy
What Cryptanalysts Can’t Do Against OTP:
- ❌ Frequency Analysis (Letters in ciphertext are uniformly distributed)
- ❌ Known-Plaintext Attacks (Even if you know part of the message, it reveals nothing about the rest)
- ❌ Chosen-Ciphertext Attacks (No mathematical relationship to exploit)
What They Can Try (And Why It Fails)
- Guessing the Key → Probability: 1 in 26^N (Impossible for N > 50)
- Side-Channel Attacks → Only works if the implementation is flawed (e.g., leaking keys via power analysis)
When Should You Actually Use OTP?
- ✅ Ultra-high-security scenarios (e.g., nuclear codes, whistleblower docs).
- ✅ Short messages where key exchange is feasible (e.g., pre-shared passwords).
- ❌ Not for: HTTPS, messaging apps, or encrypting hard drives (use AES instead).
“In 10 years of pentesting, I’ve never seen OTP broken—but I’ve seen it misused 100+ times. The weakest link is always human error.”
Real-World Applications of OTP
- Military & Espionage (Cold War-era secure comms)
- Quantum Key Distribution (QKD) – Combines OTP with quantum physics for ultra-secure links.
Practical Advice for Secure OTP Keys
Do This:
- ✅ Use a hardware RNG (or at least a high-entropy source like radioactive decay sensors)
- ✅ Verify randomness with statistical tests (NIST STS, Dieharder)
- ✅ Destroy keys after use (Burning paper pads, secure deletion of digital keys)
Never Do This:
- ❌ Reuse keys (Even once = catastrophic failure)
- ❌ Use software RNGs (Unless it’s for testing only)
- ❌ Store keys digitally (If you must, use an air-gapped, encrypted HSM)
FAQs About One-Time Pad (OTP) Cipher
- Is One-Time Pad (OTP) really unbreakable?
Yes, if used correctly. OTP provides perfect secrecy when:- The key is truly random
- The key is as long as the plaintext
- The key is never reused
- Why isn’t OTP used everywhere if it’s unbreakable?
Because of key distribution challenges. Sharing a key as long as the message securely is impractical for everyday use (e.g., encrypting large files or real-time communication). - Can OTP be cracked with quantum computers?
No. Unlike RSA or ECC, OTP doesn’t rely on mathematical hardness—it’s immune to quantum attacks. - What happens if the OTP key is reused?
Reusing a key completely breaks security. An attacker can XOR two ciphertexts to extract the plaintext (known as a “two-time pad” attack). - How is OTP different from AES encryption?
| Feature | One-Time Pad (OTP) | AES (Advanced Encryption Standard) |
|---|---|---|
| Security | Unbreakable (if used correctly) | Highly secure, but theoretically crackable with enough resources |
| Key Size | Must match message length | Fixed (128, 192, or 256 bits) |
| Speed | Slow (manual/key distribution issues) | Fast (hardware-accelerated) |
| Usage | Rare (niche applications) | Standard for most encryption today |
- Are there any real-world uses of OTP today?
Yes, but limited to:- Military & diplomatic communications (where absolute secrecy is critical)
- Quantum Key Distribution (QKD) – Combines OTP with quantum mechanics for ultra-secure links
- Can I use OTP for encrypting my emails?
Technically yes, but it’s impractical. You’d need to securely exchange a key as long as every email, which isn’t feasible for daily use. - What’s the biggest weakness of OTP?
Key management. Generating, storing, and distributing large, truly random keys securely is extremely difficult. - Has OTP ever been broken?
Only when misused (e.g., key reuse). Properly implemented OTP remains uncracked. - Is OTP better than modern encryption like AES?
For theoretical security, yes. For practical use, no—AES is faster, more scalable, and easier to implement securely.
Final Verdict: Is OTP Still Useful Today?
In my decade of experience, most cybersecurity pros agree: OTP is the most secure cipher… but also the most impractical. For everyday use, AES and RSA are better. But for absolute secrecy? Nothing beats OTP.
“OTP is like a bulletproof vest made of neutron star material. Overkill for a grocery run, but if you’re walking into a warzone, it’s the only choice.”
Want to try it? Here’s a true random key generator: random.org (uses atmospheric noise).
Want to Try It Yourself?
import random
def one_time_pad(plaintext):
key = ''.join(random.choice('ABCDEFGHIJKLMNOPQRSTUVWXYZ') for _ in plaintext)
ciphertext = ''.join(chr((ord(p) + ord(k)) % 26 + 65) for p, k in zip(plaintext, key))
return ciphertext, key
Your Turn
What’s your take on OTP? Could it ever replace modern encryption? Let’s discuss in the comments!
Leave a Reply