Data Encryption Standard (DES): How It Works, Security Flaws & Modern Alternatives
The Data Encryption Standard (DES) is a symmetric-key block cipher that shaped modern cryptography when adopted by NIST in 1977.
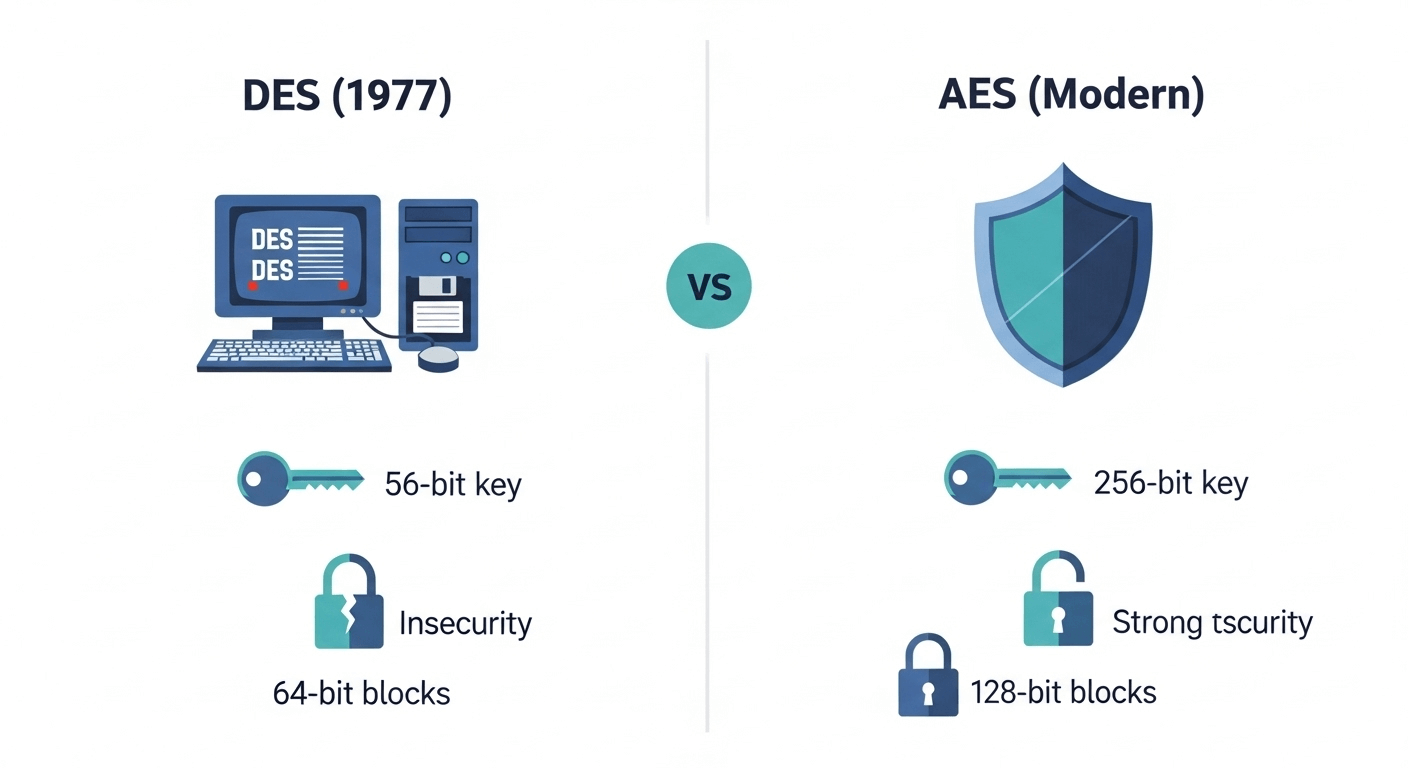
It was once widely used for securing sensitive data, but with advancements in computing power, DES’s 56-bit key became easy to break.
Today, stronger ciphers like AES have replaced it.
In this guide, you’ll learn:
- What is DES encryption?
- How DES works step by step
- The Feistel structure and why DES has 16 rounds
- DES key generation process
- Why DES is insecure today
- How DES was broken in 1998 by EFF’s Deep Crack machine
- DES vs AES vs 3DES comparison
- Modern alternatives to DES
What is DES Encryption?
DES is a symmetric encryption algorithm that converts 64-bit blocks of plaintext into ciphertext using a 56-bit secret key. The same key is used for both encryption and decryption.
Key Characteristics of DES
- Symmetric encryption (same key for sender and receiver)
- Block cipher: works on fixed-size 64-bit blocks
- Effective key size: 56 bits
- 16 rounds of a Feistel network structure
Despite being revolutionary in the 1970s, DES was cracked in 1998 by the Electronic Frontier Foundation (EFF) using brute force, leading to its replacement by AES.
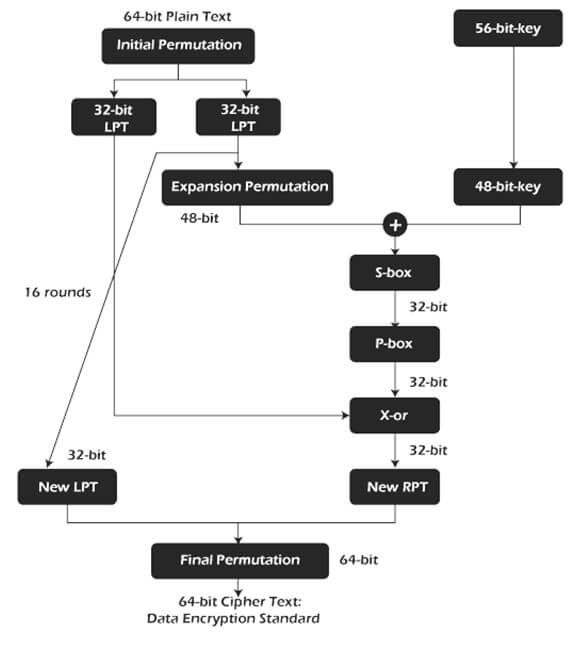
How Does DES Work? (Step-by-Step Process)
- The algorithm takes a 64-bit plaintext block.
- Initial Permutation (IP) rearranges the block according to a fixed table.
- The permuted block is split into two halves: Left Plain Text (LPT) and Right Plain Text (RPT).
- The RPT passes through the Feistel function (F) and its output is XORed with the LPT.
- The halves swap places (except in the final round).
- This process repeats for 16 rounds.
- After the 16th round, the halves are joined and a Final Permutation (FP) produces the 64-bit ciphertext.
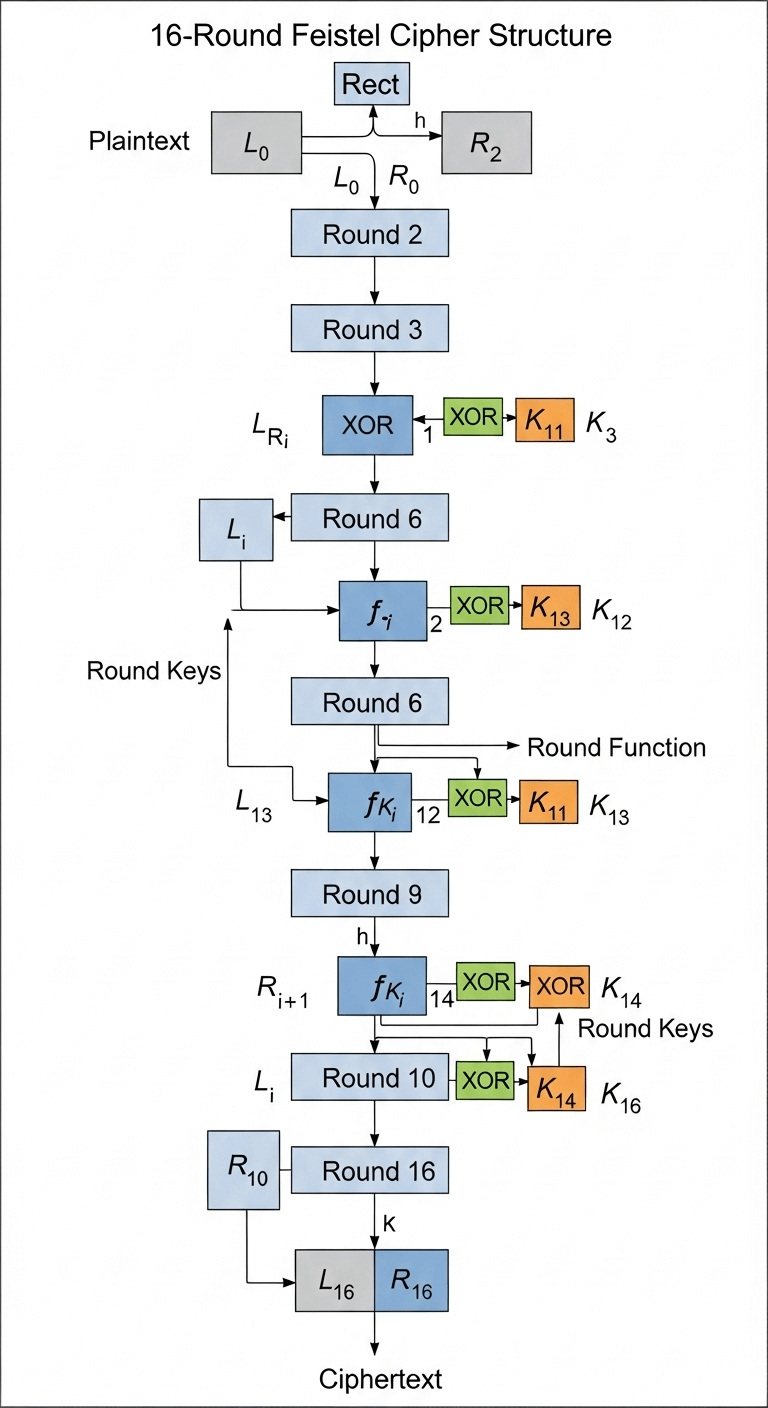
The Feistel Network: Why DES Uses 16 Rounds
DES is built on a Feistel cipher, developed by IBM in the 1970s (originally called LUCIFER). The strength of this structure lies in using the same algorithm for encryption and decryption—reversing only the round keys.
How a Feistel Round Works
- The 64-bit block splits into two 32-bit halves (LPT and RPT).
- The RPT undergoes a function:
- Expanded to 48 bits
- Mixed with a 48-bit subkey
- Processed through S-boxes (non-linear substitution)
- Permuted with a P-box
- The output is XORed with LPT, and the halves swap.
Why 16 Rounds? The Security-Performance Balance
- Confusion: S-boxes obscure the key relationship.
- Diffusion: P-boxes spread bit changes throughout the block.
- Performance: 16 rounds provided strong encryption on 1970s hardware without slowing it too much.
“DES’s S-boxes were secretly tweaked by the NSA in the 1970s. Later, academics discovered these changes made DES resistant to differential cryptanalysis—a technique unknown publicly until the 1990s.”
Feistel vs Modern Designs (AES)
| Feature | DES (Feistel) | AES (SPN) |
|---|---|---|
| Rounds | 16 | 10–14 |
| Non-linearity | S-boxes only | S-boxes + MixColumns |
| Key usage | Same algorithm for encryption and decryption | Separate key schedules |
DES Key Generation Process
DES uses a 64-bit input key, of which 8 bits are used for parity, leaving 56 bits for encryption.
Key Schedule Steps
- PC-1 Permutation: 56 bits are selected from the 64-bit key.
- Split into two 28-bit halves.
- Shift the halves left for each round.
- PC-2 Permutation: Compress into 48-bit subkeys for each round.
Weak Keys to Avoid
- All 0s or all 1s
- Semi-weak key patterns like 01FE01FE01FE01FE
Is DES Still Secure? (Security Flaws & Attacks)
1. Brute-Force Vulnerability
With only 256 possible keys, DES is vulnerable to brute force. The EFF demonstrated this in 1998.
2. Differential & Linear Cryptanalysis
Advanced attacks, such as differential cryptanalysis, can break DES with far fewer keys than brute force.
How DES Was Broken: The EFF’s Deep Crack Machine
In July 1998, the EFF built a custom machine called “Deep Crack” that cracked a DES-encrypted message in just 56 hours, proving 56-bit keys are insecure.
Deep Crack Hardware
- 1,536 custom ASIC chips, each testing 2.5 million keys per second.
- Total speed: 90 billion keys per second.
- Cost: $250,000 in 1998 (~$460,000 today).
The Attack
- Took a DES challenge from RSA Labs.
- Used known plaintext (“Strong cryptography makes the world a safer place”).
- Found the key after testing only 24% of the keyspace.
“Deep Crack was a wake-up call. It proved 56-bit keys could no longer protect sensitive data—even against non-government attackers.”
Impact of Deep Crack
- By 2006, FPGAs could break DES for under $10,000.
- NIST deprecated DES (FIPS 46-3) in 2005 and required AES or 3DES.
- Accelerated the global move to 128-bit and stronger encryption.
The Mathematics Behind the Break
| Parameter | DES (1977) | AES-128 |
|---|---|---|
| Keyspace | 256 = 72 quadrillion | 2128 = 340 undecillion |
| Time to crack | 56 hours (1998) | 1 billion years (estimated) |
| Cost | $250K (1998) | $100+ trillion (theoretical) |
DES vs 3DES vs AES – Key Differences
| Feature | DES | 3DES | AES |
|---|---|---|---|
| Key size | 56-bit | 112/168-bit | 128/192/256-bit |
| Security | Broken | More secure | Highly secure |
| Speed | Fast (1970s) | Slower | Fastest |
| Block size | 64-bit | 64-bit | 128-bit |
Why AES Won: Inside NIST’s Encryption Standard Competition
In 1997, NIST announced a competition to replace DES. The goal was to find a cipher that was faster, more secure, and free of patent restrictions.
The Finalists
| Cipher | Key Sizes | Rounds | Creator | Notable Features |
|---|---|---|---|---|
| Rijndael | 128/192/256 | 10–14 | Daemen & Rijmen | Efficient and mathematically simple |
| Serpent | 128/192/256 | 32 | Anderson et al. | Very conservative security margins |
| Twofish | 128/192/256 | 16 | Schneier et al. | Complex key schedule |
“Rijndael won because it balanced speed, security, and elegance. Its mathematical structure made it easy to analyze for backdoors—critical for government adoption.”
Why Rijndael (AES) Triumphed
- Faster than other finalists.
- S-boxes derived from math instead of arbitrary tables.
- Supports 128/192/256-bit keys for scalability.
The Legacy of the AES Competition
- AES is now standard for HTTPS, VPNs, and messaging apps.
- No practical attacks have broken AES after 20+ years.
- Open vetting of AES built trust in the algorithm worldwide.
Modern Alternatives to DES
- AES (Advanced Encryption Standard): Secure and widely used today.
- ChaCha20: Favored by Google for TLS 1.3, especially on mobile.
- RSA: Used for key exchange, not bulk data encryption.
FAQ
Is DES still used today?
Rarely. Mostly in legacy hardware systems.
Can DES be cracked?
Yes, brute-force attacks can break DES in hours.
Why was DES replaced by AES?
The 56-bit key size became too weak with advances in computing power.
What is DES encryption?
DES (Data Encryption Standard) is a symmetric-key block cipher developed in the 1970s. It encrypts data in 64-bit blocks using a 56-bit secret key.
How does DES work in simple terms?
DES works by splitting the data into two halves and processing them through 16 rounds of substitution and permutation operations (Feistel network) using a secret key.
Why does DES use 16 rounds?
DES uses 16 rounds to achieve a good balance between security and performance. More rounds provide better diffusion and confusion but slow down processing.
Is DES still secure today?
No. DES is considered insecure today because its 56-bit key can be brute-forced with modern computing power in hours or even minutes.
What replaced DES encryption?
AES (Advanced Encryption Standard) replaced DES as the modern standard. 3DES (Triple DES) was also used temporarily as a stop-gap solution.
What is the difference between DES and AES?
DES uses a 56-bit key and 64-bit blocks with 16 rounds, while AES uses 128/192/256-bit keys, 128-bit blocks, and 10–14 rounds, making AES far more secure and efficient.
What is the Feistel structure in DES?
The Feistel structure splits data into two halves and repeatedly applies a round function, swapping halves after each round. This design allows the same algorithm to be used for both encryption and decryption.
Why was DES broken in 1998?
The Electronic Frontier Foundation (EFF) built a custom machine called Deep Crack that could try 90 billion keys per second, cracking DES in 56 hours.
What is 3DES and how is it different from DES?
3DES (Triple DES) applies the DES algorithm three times with different keys, making it more secure than DES. However, it is slower and has also been deprecated.
What are modern alternatives to DES?
Modern alternatives include AES (Advanced Encryption Standard) and ChaCha20. These are faster, more secure, and suitable for modern applications.
Is AES encryption unbreakable?
AES with 128-bit or higher keys is considered secure with today’s technology. While no encryption is absolutely unbreakable, AES has no known practical attacks when implemented correctly.
Can I still use DES for learning purposes?
Yes, DES is often used in academic contexts to teach block cipher concepts, but it should never be used to protect real-world sensitive data.
Conclusion
DES was a groundbreaking encryption standard in the 1970s but has been obsolete for decades. While 3DES extended its life temporarily, AES has become the modern standard for secure encryption.
Key Takeaways:
- DES uses 56-bit keys, which are now insecure.
- AES is faster, more secure, and scalable.
- Always choose AES-256 or ChaCha20 for modern encryption needs.
Leave a Reply