Introduction: Let Me Tell You a Story About a Pizza Order
A few years back, I was working remotely from a coffee shop. My wife texted me our favorite pizza order using a string of random letters. At first, I was confused—but she explained it later: she had made up a code to stop our nosy kids from figuring it out. Funny enough, that’s cryptography in a nutshell—turning info into unreadable gibberish, unless you have the secret key.
So, what is cryptography? It’s the art and science of hiding messages to protect them from prying eyes. You use it every day—logging into websites, using WhatsApp, or even swiping your card at a store.
Let’s break down the definition of cryptography, types of ciphers, and why you should care about this digital ninja art—whether you’re a student, a teacher, or just someone who uses a computer.
What Is Cryptography? (And Why You Should Care)
Cryptography is the technique of securing communication in the presence of third parties, aka the bad guys.
Cryptography Meaning: It comes from Greek—”kryptos” meaning hidden and “graphein” meaning writing.
In Simple Words: It means writing or transmitting something in a way that only the intended recipient can understand.
Example: Ever used WhatsApp? Its messages are encrypted with end-to-end encryption. Even WhatsApp can’t read your texts.
A Quick Real-World Case Study
According to a 2023 report from Forbes, over 85% of global data breaches could have been avoided with proper encryption. That’s wild. (Source: Forbes Technology Council, 2023)
Core Goals of Cryptography – (CIAN) Confidentiality, Integrity, Authentication, Non-repudiation
Cryptography isn’t just about keeping secrets—it’s about securing digital trust. It’s built on four foundational principles:
Confidentiality: Keeps data hidden from unauthorized access using encryption.
Integrity: Ensures data hasn’t been altered during transmission or storage.
Authentication: Confirms identity—of a person, device, or message source.
Non-repudiation: Prevents someone from denying their digital actions.
These are achieved using encryption algorithms, digital signatures, and hashing. Back in the day, the focus was just on hiding secrets. But now, with all our lives online, trust, verification, and accountability are just as important.
This evolution shows how cryptography has matured into a vital pillar of internet trust—from emails and eCommerce to digital voting and legal contracts.
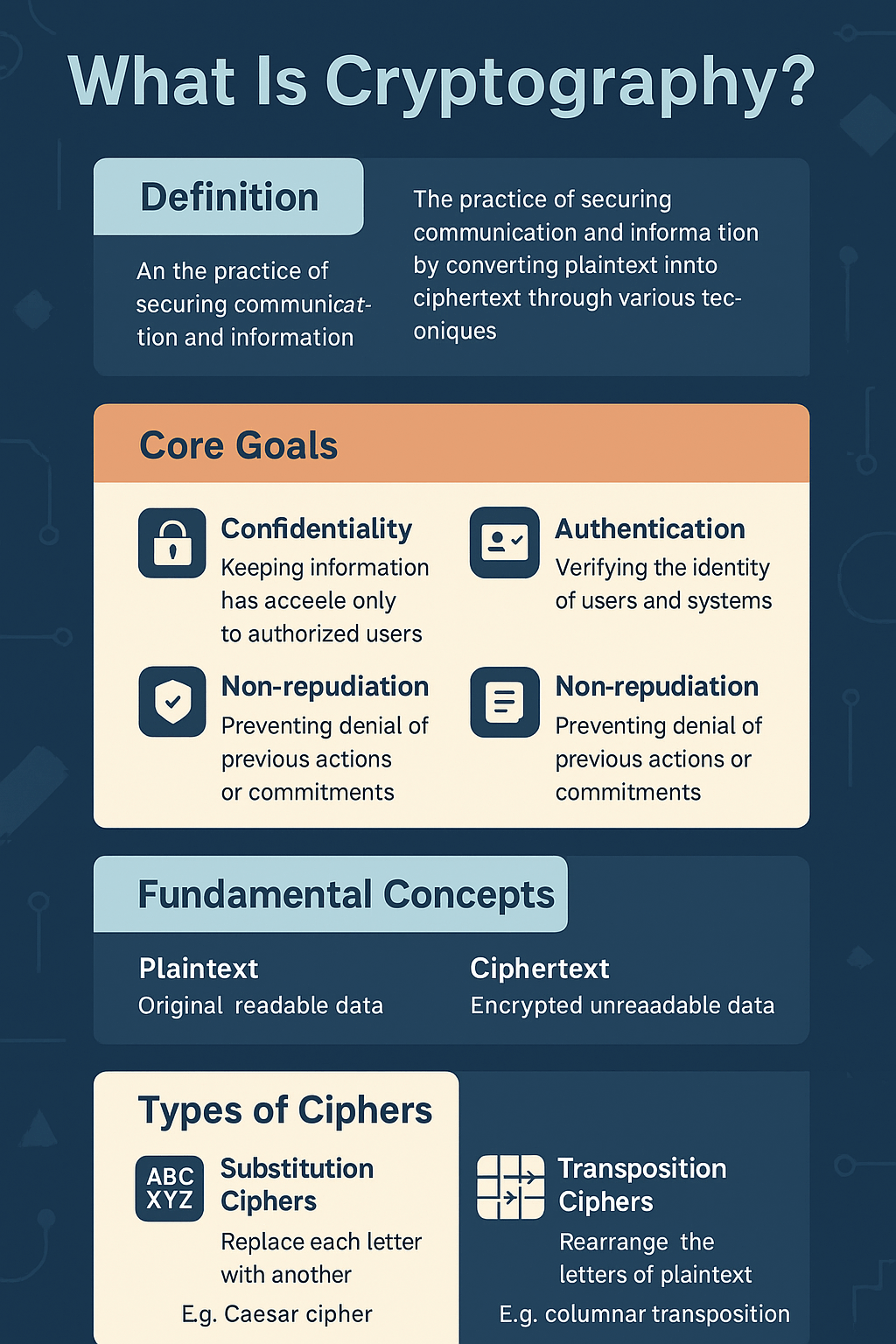
Fundamental Concepts: Keys, Plaintext, Ciphertext, , Algorithms
Before we jump into types of cryptography, let’s nail down some basics:
- Plaintext: The original message or readable data.
- Ciphertext: The encrypted, unreadable version of the plaintext.
- Encryption: Converting plaintext into ciphertext using a key.
- Decryption: Converting ciphertext back into plaintext using a key.
Keys
- Symmetric Keys: Same key for both encrypting and decrypting.
- Asymmetric Keys: One public, one private—used for encryption and decryption.
Algorithms (a.k.a. Ciphers)
These are the rules and steps used to scramble and unscramble data. Examples? AES, RSA, and ECC.
Modern cryptography follows Kerckhoffs’s Principle: The system’s security should depend on the secrecy of the key—not the algorithm. In plain English: it’s better to use publicly known algorithms that have been tested to death by experts, rather than trying to hide how your code works.
Types of Cryptography
Here’s the deal—modern cryptography can be divided into three main types:
1. Symmetric Key Cryptography
One Key is used to encrypt and decrypt.
Fast, but risky if the key is leaked.
Example: AES (Advanced Encryption Standard)
2. Asymmetric Key Cryptography
Uses two keys—a public key (shared) and a private key (kept secret).
Slower but more secure.
Example: RSA (Rivest–Shamir–Adleman)
3. Hash Functions
No keys involved.
Takes data and produces a fixed-length string—called a hash.
Used for verifying data integrity.
Example: SHA-256 (used in Bitcoin)
In my experience, most beginners overlook the importance of hash functions, even though they power password storage and blockchain tech.
What Are Ciphers? (And Why They Matter)
Cipher Definition:
A cipher is the method or algorithm used to perform encryption and decryption.
- Think of it like a recipe for turning normal text (plaintext) into code (ciphertext).
Types of Ciphers:
1. Substitution Cipher
A substitution cipher replaces each character in the plaintext with another character. It’s simple but prone to attacks like frequency analysis. Caesar Cipher is the classic example.
2. Transposition Cipher
Instead of replacing letters, transposition ciphers rearrange their order. Think of Rail Fence Cipher. Not secure alone, but adds a layer of obscurity.
3. Block Cipher
Encrypts fixed-size blocks of data. AES is a top example. Highly secure and used in HTTPS, VPNs, and more.
4. Stream Cipher
Encrypts data bit-by-bit. Great for live data like VoIP. ChaCha20 is a modern go-to.
Which cipher is most used? That’s easy—AES. It’s used by the U.S. government and approved by NIST.gov.
Cryptanalysis and Modern Counter measures
Cryptanalysis is the science of breaking codes—either to test their strength or exploit their weaknesses. It’s a never-ending duel between code makers and code breakers.
Common Attack Vectors
Brute-Force Attacks
Frequency Analysis
Known-Plaintext Attacks
Side-Channel Attacks
Chosen-Plaintext & Chosen-Ciphertext Attacks
Credential Stuffing
How Modern Cryptography Fights Back
Today’s algorithms rely on math problems that are nearly impossible to solve without the key. That includes:
RSA, ECC, AES, and TLS/HTTPS
Use of MFA, key rotation, audits, and Post-Quantum Cryptography (PQC)
Emerging tech like Quantum Key Distribution (QKD)
Real-Life Uses of Cryptography
Messaging: WhatsApp, Signal
Banking: Online transactions, chip cards
Emails: PGP
Disk Encryption: BitLocker
Crypto: Bitcoin and Ethereum
FAQ: Quick Answers to Common Cryptography Questions
What is cryptography meaning?
It’s the practice of protecting information through encryption.
What is cryptography in simple words?
Turning messages into secret codes that only the right person can read.
What is cryptography used for?
Securing data, communications, payments, and identities.
What is cryptography in computer security?
It’s the foundation of secure systems—protecting login info, files, and more.
What are the three types of cryptography?
Symmetric, asymmetric, and hashing.
What are types of ciphers?
Substitution, transposition, block, and stream ciphers.
What is the most used cipher?
AES—it’s used in government, browsers, and mobile apps.
What is cipher definition?
A method or formula for encrypting and decrypting data.
Which cipher is secure?
AES and ECC are highly secure when used correctly.
Is SSL a cipher?
No, but it uses multiple ciphers during encryption.
Final Thoughts (And a Friendly Nudge)
In my decade of experience, most beginners overlook the basics—keys, hashes, and how real-world ciphers work. Now that you’ve got a grasp on cryptography, here’s what I recommend:
✅ Start using password managers. ✅ Enable MFA everywhere. ✅ Understand how HTTPS protects your data.
Got questions or curious about implementing encryption on your app or website? Reach out—Calc Toolify is here to help you demystify the tech, one tool at a time.
Leave a Reply